Certbot used to be the go-to tool to install Let’s Encrypt SSL and periodically update them. However, now they require snapd to install the latest version of certbot.
Installing snapd is impossible (or not that I know of) on Amazon AWS EC2 running Amazon Linux at the time of writing.
So let’s use GetSSL (This is suggested in Let’s Encrypt documentation)
Warning: I am no server expert. This is a documentation of how I did it. Please use caution and do your reading. I use Apache.
Install GetSSL
I downloaded GetSSL and made it executable as per their documentation.
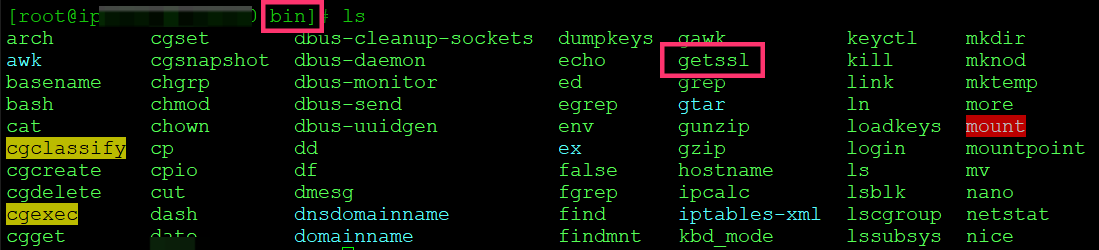
curl --silent https://raw.githubusercontent.com/srvrco/getssl/master/getssl > getssl ; chmod 700 getsslTo have access to GetSSL from anywhere, I moved it to the /bin folder. This means you can type getssl from anywhere. Just like how you would run other linux commands.
To move:
mv -i getssl /bin
Configuring GetSSL
Now we have the tools to do it. Time to put it to work. I followed this part of GetSSL documentation.
getssl -c yourdomain.com
Even if you use www.yourdomain.com, make sure you simply enter the top level domain only (i.e yourdomain.com without the www). Sub-domains can be added in the configuration.
If things go well some configuration files will be created and the location will be displayed on screen. It looks very much like:
~/.getssl
~/.getssl/getssl.cfg
~/.getssl/yourdomain.com
~/.getssl/yourdomain.com/getssl.cfgThere are two levels of configuration. It’s quite simple, don’t worry.
- One general configuration that applies to all domains. This is in ~/.getssl/getssl.cfg
- One domain level configuration that only applies to the specific domain. This is in ~/.getssl/yourdomain.com/getssl.cfg
Configuring ~/.getssl/getssl.cfg
- Un-comment this line: CA=”https://acme-v02.api.letsencrypt.org”
- Added the ACCOUNT_EMAIL
- Added the command to reload after certificate update: RELOAD_CMD=”sudo service httpd restart”
Configuring ~/.getssl/yourdomain.com/getssl.cfg
- Added sub-domain to the SANS list as: SANS=”www.yourdomain.com”
- Added ACL as: ACL=(‘/var/www/html/yourdomain.com/wordpress/.well-known/acme-challenge’)
- Set USE_SINGLE_ACL as “true”
Note: /var/www/html/yourdomain.com/wordpress/ is where I have installed WordPress. Refer: How I manage WordPress websites with Git, GitHub and Local
Adding SSL Certificate
Now that you have GetSSL and it’s configured, all it takes is to run:
getssl yourdomain.com
I had my certificate and key file saved in the following files respectively along with some other stuff.
/root/.getssl/yourdomain.com/yourdomain.com.crt
/root/.getssl/yourdomain.com/yourdomain.com.keyUpdating VHosts
This totally depends on your specific setup. I will document what is mine. Yours might be similar.
VHosts were located at /etc/httpd/conf.d
Redirect HTTP to HTTPS by editing vhost.conf
<VirtualHost *:80>
ServerName yourdomain.com
ServerAlias yourdomain.com *.yourdomain.com
DocumentRoot /var/www/html/yourdomain.com/wordpress
ServerAdmin my-email@gmail.com
ErrorLog "logs/yourdomain.com-error_log"
CustomLog "logs/yourdomain.com-access_log" common
<Directory /var/www/html/yourdomain.com/wordpress>
AllowOverride All
</Directory>
RewriteEngine on
RewriteCond %{SERVER_NAME} =*.yourdomain.com [OR]
RewriteCond %{SERVER_NAME} =yourdomain.com
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
</VirtualHost>Adding the SSL certificate in vhost-le-ssl.conf
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName yourdomain.com
ServerAlias yourdomain.com *.yourdomain.com
DocumentRoot /var/www/html/yourdomain.com/wordpress
ServerAdmin my-email@gmail.com
ErrorLog "logs/yourdomain.com-error_log"
CustomLog "logs/yourdomain.com-access_log" common
<Directory /var/www/html/yourdomain.com/wordpress>
AllowOverride All
</Directory>
SSLCertificateFile /root/.getssl/yourdomain.com/yourdomain.com.crt
SSLCertificateKeyFile /root/.getssl/yourdomain.com/yourdomain.com.key
SSLCertificateChainFile /root/.getssl/yourdomain.com/chain.crt
</VirtualHost>
</IfModule>Restart Apache
sudo service httpd restart
Automate Certificate Renewals
Easily possible with a cron job. But before that, you will need to find two things.
- First, the current
PATH. To do so simply typeecho $PATHin the terminal. Make a note of this. (Mine was/sbin:/bin:/usr/sbin:/usr/bin:/opt/aws/bin) - Secondly, the absolute path to the working directory with the global getssl.cfg file. To find that, navigate to the folder by
cd ~/.getssland typeecho $PWD. Make a note of the path. (Mine was/root/.getssl)
To see and edit all Cron jobs: vim /etc/crontab
At the top of the file, there might be a PATH mentioned. Check if it matches the PATH you copied from the terminal before. If not, update the missing paths.
If PATH is mentioned in crontab, then you can add a PATH at the top of the file (refer). This is what I have.
PATH=/sbin:/bin:/usr/sbin:/usr/bin:/opt/aws/bin
Now add a weekly cron:
0 0 * * 0 root getssl -w /root/.getssl -U -a -q
where:
- -w /root/.getssl is the working directory, the one that contains
getssl.cfgand other domain folders, which we found out previously. - -U disables automatic updates to getssl.
- -a updates certificates of all domains.
- -q enables quiet mode so that the script works silently.
- You can refer the documentation for further details on these options.
That did it for me. I hope that it helped you. Good luck!





This was super helpful! Thank you so much for the write up
Very happy to hear that Jared. Thank you for letting me know!